In today’s interconnected world, cyber threats are becoming increasingly prevalent, and software vulnerabilities are often targeted by attackers seeking to exploit them for various purposes. Secure software development helps to protect against these threats by minimising the risk of vulnerabilities being introduced into the software.
Several strategies, tools, and techniques are used in secure software development to produce software that is resistant to suspicious attacks, unauthorised access, and data breaches. Every phase of the software development lifecycle, from design and coding to testing and deployment, should incorporate security considerations.
At every level of the development process, possible security risks and vulnerabilities must be identified to incorporate mitigation measures. Using secure coding techniques, conducting regular vulnerability assessments and penetration tests, and putting security tools like authentication and access controls in place are some examples of this. In order to keep the software secure and up to date with the most recent security patches and updates, secure software development also involves ongoing monitoring and maintenance of the program.
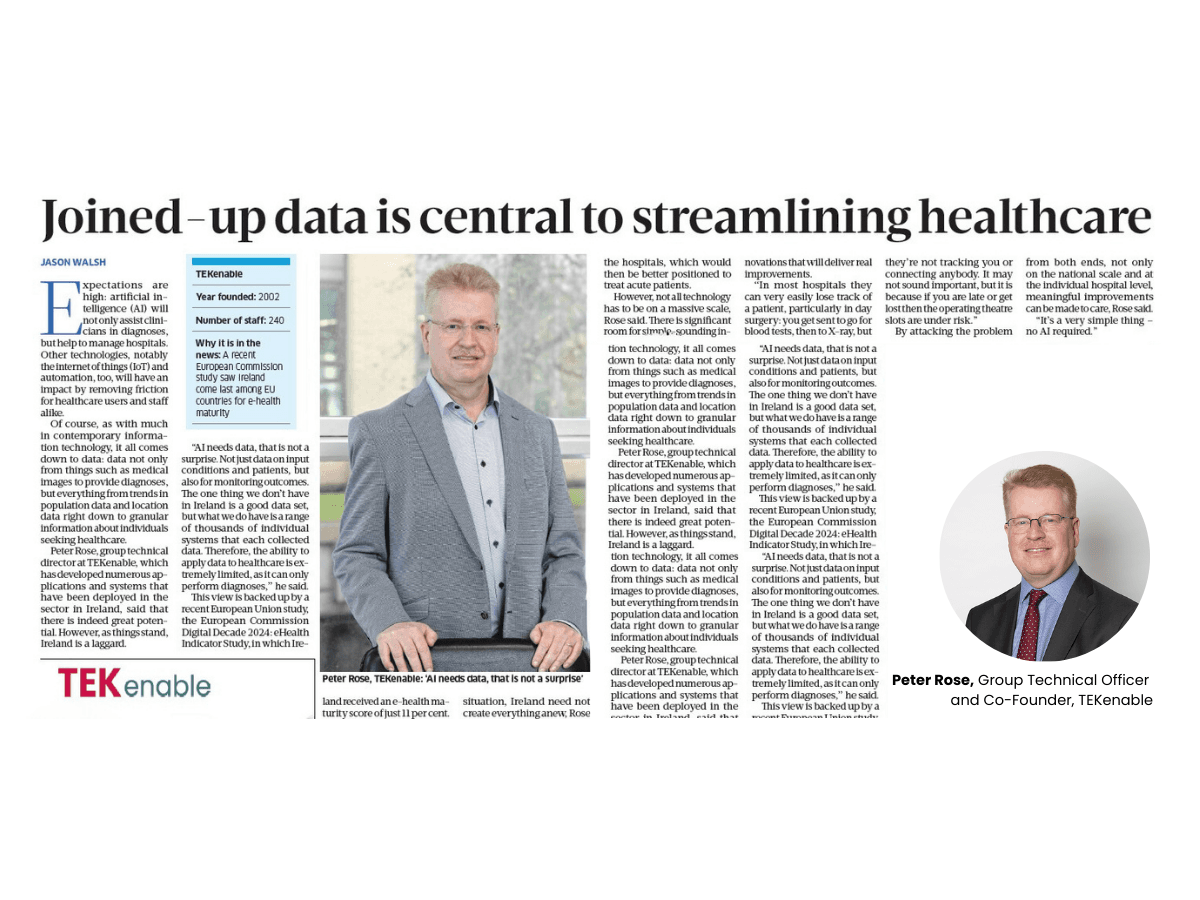
“We don’t deliver security as a service, but we deliver secure software by standard” – Peter Rose, CTO TEKenable.
To prevent unauthorised access, modification, or theft of sensitive data, secure software development is used. Personal information, financial data, and confidential business information are all included. Moreover, it can assist avoid cyber-attacks such as malware, ransomware, and phishing. Businesses can suffer considerable financial and reputational damage as a result of these attacks. Implementing secure software development methods early in the development process can help to lower the cost of later security fixes. This can also help to avoid expensive legal battles and reputational harm. Many industries are governed by regulations that necessitate the use of secure software development practices. Compliance with these regulations can aid in avoiding legal ramifications and fines.
By developing secure software, businesses can build trust with their customers. This can lead to increased customer loyalty and positive word-of-mouth referrals. Secure software development practices can also lead to better-quality software. By identifying and addressing security vulnerabilities during the development process, organisations can also address other potential issues and ensure that the software meets the needs of its users. Overall, secure software development is essential for protecting sensitive data, maintaining the integrity of software applications, and ensuring the privacy and security of end users.
Steps to secure software development
- Define Security Requirements: Establish security requirements that should be met throughout the development process. This can be done by identifying potential threats, assessing the risk associated with each threat, and specifying security controls to mitigate the risks.
- Design Secure Architecture: Incorporate security into the software architecture by implementing secure coding practices, design patterns, and techniques. The architecture should be designed to limit attack surfaces, provide isolation and segmentation, and prevent vulnerabilities.
- Use Secure Coding Practices: Write secure code that adheres to secure coding practices. This includes input validation, error handling, and avoiding common coding errors like buffer overflows and SQL injection.
- Test for Security: Perform security testing throughout the development process, including unit testing, integration testing, and acceptance testing. This should include vulnerability scanning, penetration testing, and code analysis.
- Follow Secure Deployment Practices: Following secure deployment practices when deploying the software. This includes using secure communication protocols, securing the hosting environment, and applying security patches and updates.
- Continuously Monitor for Security: Monitoring the software for security vulnerabilities and incidents after deployment. This can include using intrusion detection and prevention systems, log analysis, and security information and event management (SIEM) tools.
Security cannot be added to software after it has been built. At TEKenable, we start with the end goal in mind – beginning with a clear understanding of the risks and needs of the software application and embedding security at each stage – from architecture, design, implementation, and the testing process. We call this our Secure Software Development Life Cycle (SSDLC).

All the software that we develop is in compliance with ISO27001:2013 and resistant to the OWASP Top 10 attacks. We use automated penetration testing and static code inspection as part of DevSecOps, and our solutions are often tested by third-party security companies as part of our customer acceptance testing. We hold CISSP, CISM and CSSLP certifications as well as ISO9001, ISO27001, ISO13485, IEC62304 and Cyber Essentials Certifications as proof of our commitment to cyber security.
At TEKenable, we take security seriously. We understand that software vulnerabilities can lead to serious consequences, including data breaches, financial loss, and damage to a company’s reputation. That’s why we prioritize secure software development practices in everything we do. We have a track record of success in delivering secure software solutions for businesses of different sizes and industries. Our team of experienced developers and security experts are passionate about what they do, and they are always learning and adapting to stay on top of the latest threats and technologies. We work closely with our clients to understand their specific security needs and requirements and tailor our approach accordingly.