True cybersecurity starts from square one, with security built into applications in the design and development stage
Not all software comes from global giants like Microsoft, Salesforce or Adobe. In fact, most of it doesn’t. According to some estimates, as much as 90 per cent of software in use in the world was developed for specialist uses inside businesses – and stayed within those enterprises.
Given that, what role does security have in software development?
In reality, when we talk about cybersecurity today we tend to focus on the network infrastructure rather than the code that is running on it. And yet, that very software is a key vector for breaches.
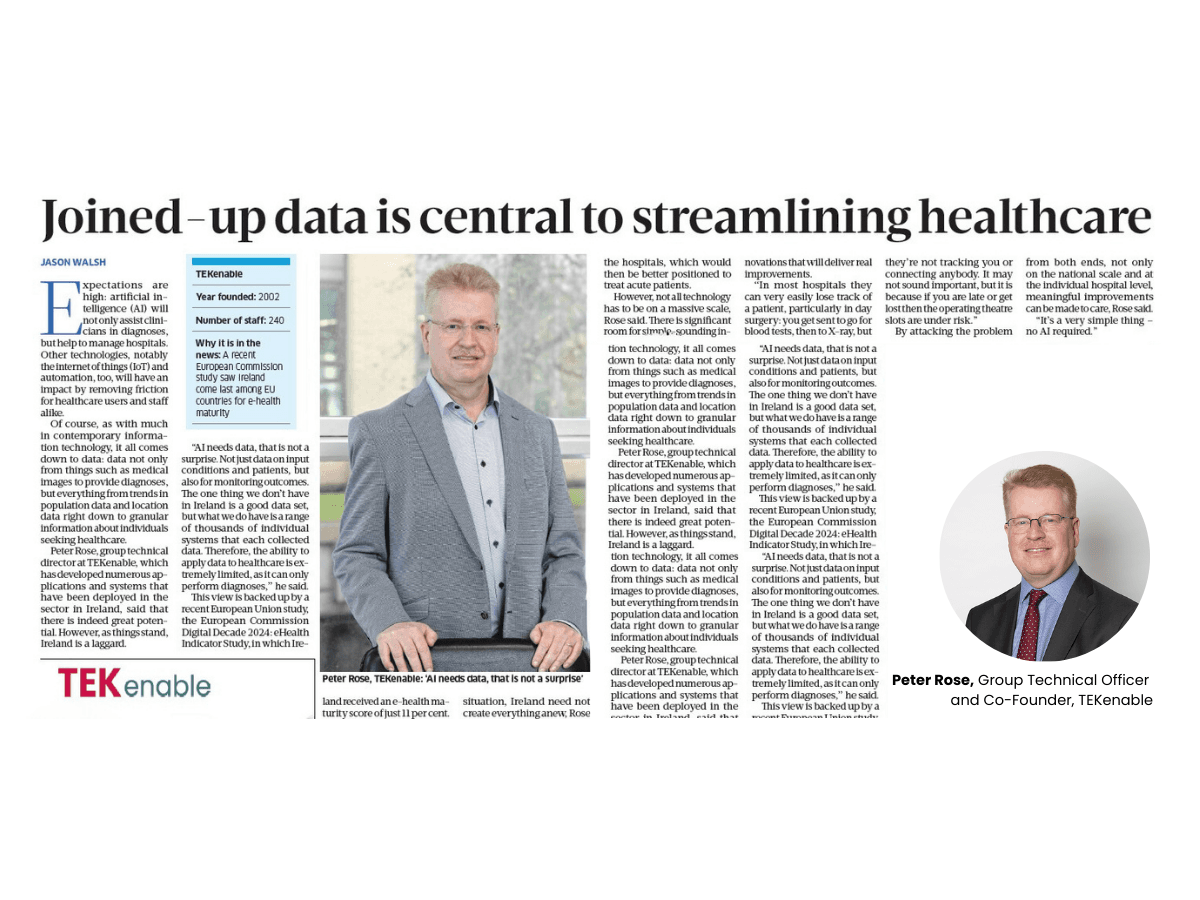
“Most people think of cybersecurity today as a box with blue flashing lights. The truth is, whatever you buying, it’s about a lot more than that,” said Peter Rose, group chief technology officer at custom development specialists TEKenable.
Rose said TEKenable want to edit to be better understood that security needs to be an essential component of good development.
“We have a secure software methodology [because] it is not possible to retrofit security into a software product, “he said.
It seems obvious, so what is holding things back? Security too often simply takes a back seat to get things done, said Rose. But this could be changed by demanding security from development partners.
“We think there’s a big element missing from procurement and that is around the ability of a company to deliver software securely from day one,” he said.
Secure software is not more expensive than insecure software: you have the same amount of code and write it with more forethought. It needs to be featured in the procurement – Peter Rose, TEKenable
“Someone asks for something to be delivered, whatever it is, and all the effort is spent on delivering that, and not on the risks associated with it.”
Rose said that businesses developing software, or outsourcing it to others, need to perform a proper assessment of the risks that it can bring to their operations.
“Have you considered the management and governance around that software? It’s our contention that a lot of the systems that are being delivered to companies are not delivered correctly. We’re very much of the opinion that it should be a hygiene factor, just standard,” he said.
If the procurement process is at fault, however, it seems to be a question of ignorance more than anything else. Developing for security from day one does not add to the cost of creating and deploying software, Rose said.
“We’ve found that price is still the main consideration. The thing is, it’s not expensive to add into the process.”
Potential risks from software include data exposure, financial fraud and, intriguingly, shutdown or control of foyer-physical systems that operate mechanical switches.
In other words, internet of things (IoT) devices, which are often poorly secured and unsupported, interact through software with all manner of company information and physical processes inside businesses.
“Industrial control equipment was never designed for security, and it was never designed for upgradability, and it’s out there and accessible in the world,” Rose said.
“The bottom line is secure software is not more expensive than insecure software: you have the same amount of code and write it with more forethought. It needs to be featured in procurement.”
For Rose, the goal is to drive forward secure development in the face of what can often seem a lack of interest, both from the industry and end-users.
“We don’t deliver security as a service, but we deliver secure software by standard, “he said.
The above text is reproduced from news article authored by Jason Walsh and published in Sunday Business Post, dated 20th November 2022.